Mission Accomplished.
Thank you. You are all set!
Keep an eye on your inbox.
Your follow-up email with login detaisl is on its way.
Please check your spam folder if you don’t get an email in the next 10 minutes.
Do you have colleagues or peers who might be interested in attending the webinar? Email them or share the registration page so they can join, too.
If you have any questions about the webinar or suggestions, mail our marketing lady, Ursula, at [email protected].
While you're here, learn more. read on. explore further.
Complimentary analyst report
On the Radar: Nokod offers security for low-code, no-code apps
Rik Turner, senior principal analyst at Omdia, evaluates Nokod’s platform and its coverage of vulnerabilities and risks in low-code and no-code apps.

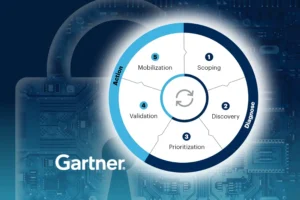
Bridging the Gap: Integrating LCNC Apps into the CTEM Framework
The rapid adoption of low-code/no-code (LCNC) development and robotic process automation (RPA) presents unique cybersecurity challenges. Incorporating LCNC and RPA into the Continuous Threat Exposure Management framework can help mitigate associated risks effectively.

The Attacker’s Path to Hacking UiPath RPAs
Leaving the attack surface created by UiPath robotic process automations unattended is more dangerous than you might think.
In this webinar, security expert Amichai Shulman demonstrates key RPA weaknesses, such as SQL injection, command injection, supply chain vulnerabilities, and container security flaws.

Empowering Cybersecurity Teams with Nokod’s Latest Open-Source Assessment Tools
Nokod Security is happy to introduce its growing suite of Power Platform assessment tools helping security teams quickly evaluate the size and scope of the attack surface created by citizen development within their organization.
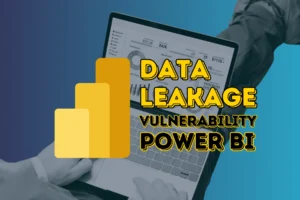
In Plain Sight: How Microsoft Power BI Reports Expose Sensitive Data on the Web
The Nokod Research Team discovered a data leakage vulnerability in the Microsoft Power BI service which potentially affects tens of thousands of organizations and which allows anonymous viewers on the Internet to access sensitive data, including employee and business data, PHI, and PII.

Power Hacking with Microsoft Power Platform
Make sure that your Power Platform low-code and no-code development doesn’t translate to low security. Watch this webinar and join security expert Amichai Shulman for a deep dive into real-world attacks, exposing dangerous misconceptions and busting the myth that Power Platform apps aren’t creating an external attack surface.
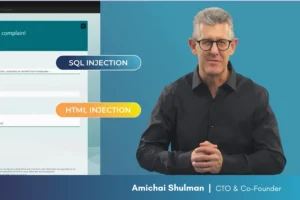
The Unbearable Stubbornness of SQL Injection Vulnerabilities
CISA and FBI issued a stern warning to eradicate SQL injection vulnerabilities for good. How, with code scanners in place and ongoing security training for developers, does this problem persist? Read our take predicting that the numbers of SQLi attacks will likely rise.
