Introduction
During Cybersecurity Awareness Month, we tend to underscore the critical importance of implementing robust cybersecurity practices. As cyber threats evolve at an unprecedented rate, organizations and security teams must adapt swiftly to safeguard their assets and data effectively. Citizen development is the most significant paradigm shift in application development with a rapidly growing attack surface.
In response to these challenges, Nokod Security is happy to introduce its growing suite of Power Platform assessment tools this month. These tools are designed to assist security teams in evaluating risks within Power Platform development environments, providing valuable insights to address the growing concern of shadow engineering.
Nokod’s New Security Discovery Tool for Power Platform
When discussing the security risks of citizen-developed apps and automations on Power Platform, security professionals often find themselves in a challenging position. While they understand the potential threats, they frequently lack the necessary visibility and tools to assess the scope and impact of these risks within their organization. This knowledge gap creates a significant barrier to prioritizing this growing attack surface and leaves many vulnerabilities without effective risk management and mitigation.
To address this issue, Nokod offers its open-source, lightweight discovery and assessment tool. It provides security teams with much-needed insights into their organization’s Power Platform usage, scope, and seize of their internal and external attack surface, as well as highlights sample vulnerabilities.
Unlike tools that require full integration into the Power Platform, Nokod’s tool runs from a local machine with read-only permission, ensuring a lightweight and quick assessment.
And we kept it easy: Users only need to run simple Python commands to execute a scan, making the tool accessible even for those with less technical expertise. You’ll find information about the tool (incl. links to GitHub, installation video, etc.) here.
Insights Gained from Your Power Platform Scan Results
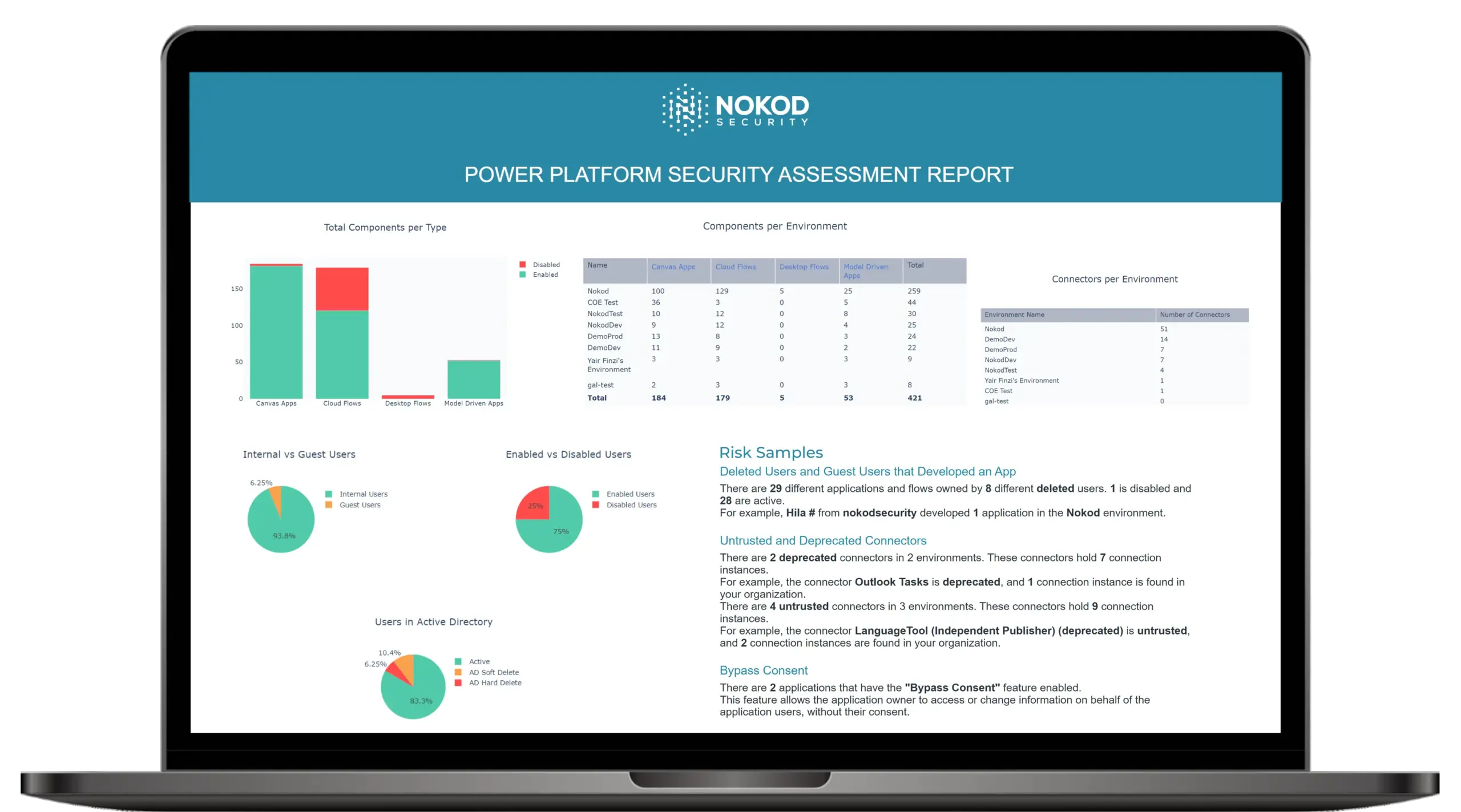
Running the quick assessment generates a report that gives you an overview of the current situation. Besides the total number of environments in your organization, the report lists the following data points for your top ten environments:
- Name, type, creator, creation, and last activity time of the environment
- What components like canvas apps, could flows, desktop flows, and model-driven apps exist, and how are they distributed across the top-ten environments
- Number of connectors used per environment
- User statistics such as internal vs. guest users, enabled vs. disabled, user status on Active Directory
- Number of developers in the three biggest environments
- Top three most used connectors
Discovering all Power Platform assets, the report also provides insights into potential risks, such as:
- Deleted or Guest Users Developing Apps: The tool identifies apps created by users no longer with the organization, which may pose a security risk.
- Untrusted and Deprecated Connectors: It detects connectors that could introduce vulnerabilities or allow unauthorized access.
- Bypass Consent: This compliance issue arises when the application owner has access to or can change information on behalf of the application users without their consent.
Power BI Analyzer – Completing the Picture
In addition to the Attack Surface Assessment Tool, Nokod previously published two free essential tools to enhance Power BI security. The two versions of Power Analyzer analyze the reports’ underlying data models to identify unused columns or tables in visualizations/reports. When reports are overshared internally or published to the web, this can easily expose sensitive data.
These tools are particularly crucial given that a recent data leakage vulnerability in Power BI could affect thousands of organizations. Reports with hidden sensitive data can give unauthorized access to filtered data records, which could lead to data leakage both internally and externally.
You’ll find information about the tool (incl. links to GitHub, installation video, etc.) here.
Watch our video to learn more about how attackers can hack Power BI reports published to the web to get access to hidden data.
Take a Proactive Security Approach
Nokod’s open-source suite of discovery tools for Power Platform and Power BI is primarily designed for security teams, who are at the forefront of tackling shadow engineering. However, platform administrators and the owners of a company’s Power Platform environment can also benefit from their use.
Our goal is to help security teams quickly assess the size and scope of the attack surface created by citizen development within their organization. By offering visibility and identifying potential vulnerabilities, we hope to enable security professional to take a more informed and active approach to protecting their critical assets and data.
For further inquiries, please contact us at [email protected] or schedule a demo.
Join Us on Our Journey
Subscribe to Our Newsletter – Stay informed about the latest security trends, product updates, and industry insights. Find a signup form in the sidebar.
Follow Us on LinkedIn – Connect with us on LinkedIn for real-time updates and engaging discussions.


