What is CTEM?
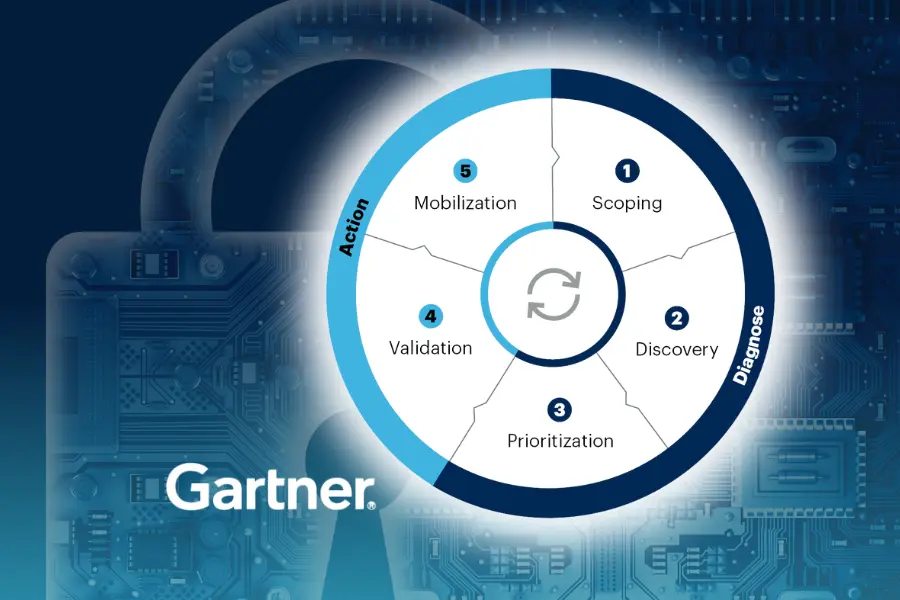
CTEM, which stands for Continuous Threat Exposure Management and is a concept introduced by Gartner, enables organizations to proactively assess and manage their security posture by continuously monitoring cybersecurity threats. The CTEM approach includes five stages: scoping, discovery, prioritization, validation, and mobilization. Using CTEM, enterprises can improve their security posture by integrating risk management into a continual assessment and action cycle.
Why LCNC Security Should Be Part of CTEM
Today, any employee, aka “citizen developer,” can easily create applications and automate workflows. This democratization of app development leads to “Shadow Engineering,” meaning that IT and security teams have little to no visibility into these LCNC environments. This significantly expands an enterprise’s internal and external attack surface, and unfortunately, most companies don’t have the right tools to reduce these risks. Even the most developed application security stack and processes fail to cover LCNC risks well.
Gartner’s recent survey reports that 64% of CIOs have already deployed LCNC technology or are planning to deploy it within the next two years. So, on the one hand, senior management is embracing citizen development and is allowing “Shadow Engineering” to expand in their organization. On the other hand, they may not be aware of the severity of the risks its use brings.
This widespread adoption of LCNC puts enterprises at risk if they don’t fully understand how to monitor these applications and automations for potential threats and vulnerabilities. By bringing LCNC applications and RPAs under the CTEM umbrella, enterprises can more effectively detect exploitable vulnerabilities and prioritize remediation efforts based on business impact.
Applying the CTEM Framework to LCNC Security
CTEM aims to improve threat exposure management by adopting a holistic perspective and surpassing conventional vulnerability assessment methods. This comprehensive and continuous process proves beneficial in addressing the dynamic nature of LCNC app development, which presents distinct security challenges. Throughout the five stages of CTEM implementation, it’s crucial to factor in the unique dynamism inherent to LCNC.
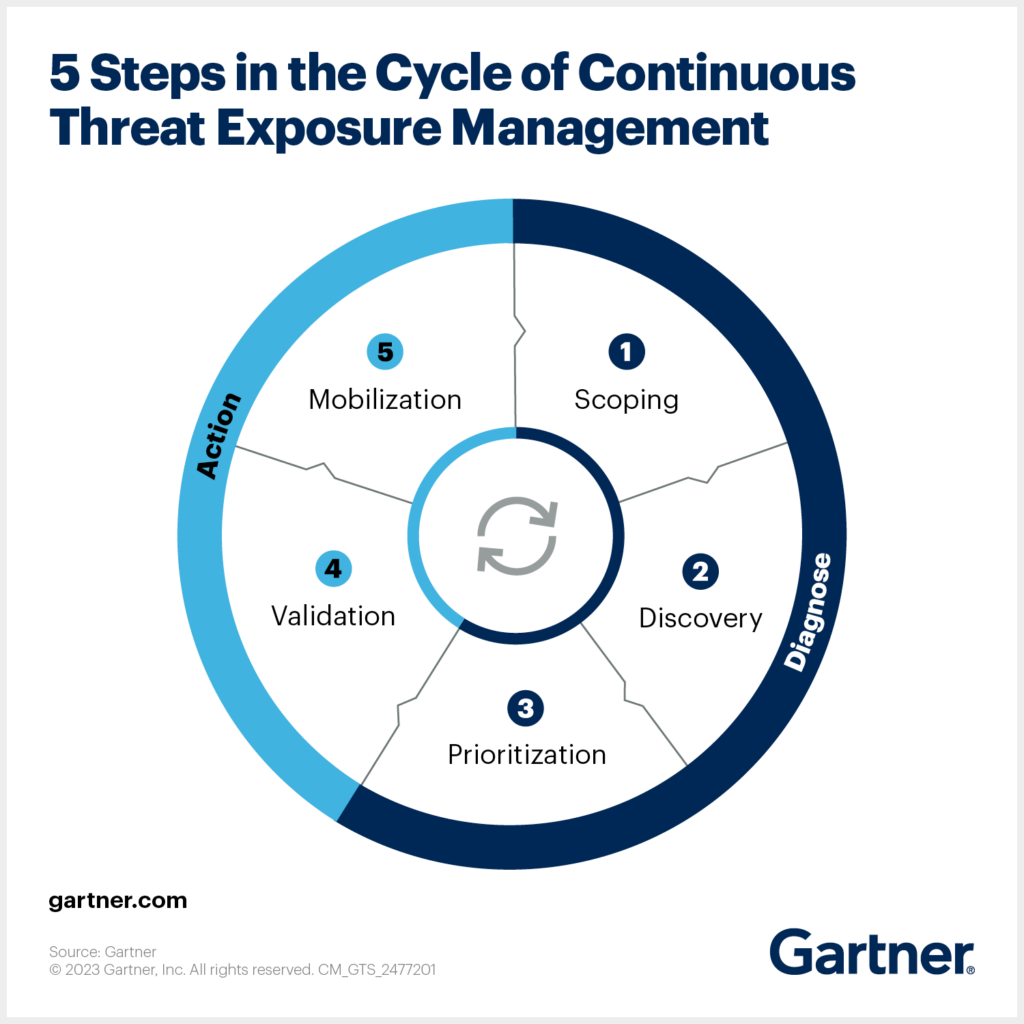
1. SCOPING
Start by evaluating the business criticality of LCNC and RPA assets to determine which should fall under CTEM oversight. Consider specific sets or groups of users, connections, connectors, applications, workflows, and automated processes. You can also segment these assets based on various factors such as business context, organizational division, platform environment, or geographical location.
2. DISCOVERY
After identifying the scope, focus on identifying and documenting visible and hidden assets, vulnerabilities, and misconfigurations. Limited visibility into LCNC applications and automations can pose challenges in mapping LCNC activities and maintaining an up-to-date inventory of platform-related assets. Continuous scanning for threats, risks, and security issues is crucial, as well as sharing comprehensive details with all the relevant stakeholders to support subsequent model stages. Issue discovery may require a policy engine, informed by application security research and expertise, to adequately uncover and address security issues.
3. PRIORITIZATION
After scoping and discovery, you will have a clear picture of the vulnerabilities within your enterprise. However, to ensure CTEM’s success, effective prioritization of these vulnerabilities is essential. Ranking security vulnerabilities requires evaluation of urgency, impact, severity, existing safeguards, risk appetite, and your enterprise’s cumulative risk posture. Since pre-defined traditional scoring systems are insufficient for LCNC, prioritization should combine conventional risk metrics with platform-specific and organizational factors.
As a baseline, it is recommended to use a recognized scoring framework like CVSS. Still, scores should be adjusted to account for factors such as accessibility, application status (enabled or disabled), and deployment context (e.g. production vs. development). Remember that prioritization is crucial in LCNC due to the sheer scale of threats, the multitude of assets, and the generally limited security proficiency of app developers, all of which contribute to misconfigurations and security gaps within LCNC applications and automations.
4. VALIDATION
The validation phase focuses on three key goals:
- Confirming the exploitability of the identified vulnerabilities
- Evaluating the potential consequences of defense failures
- Establishing robust incident response protocols
While LCNC applications share many validation practices with traditional software–including penetration testing, red team exercises, and simulations–they present unique challenges due to their visual development interfaces, accelerated deployment cycles, and heavy use of pre-built components. As a result, specialized validation techniques are necessary to address these LCNC-specific security considerations effectively.
5. MOBILIZATION
In LCNC application security, effective mobilization will mean alerting business users and citizen developers of security issues and giving them appropriate remediation tools to resolve them. This approach recognizes that security teams, while essential, cannot solely manage the myriad of potential issues due to their limited familiarity with LCNC environments and the nuanced permission models that often require direct owner intervention.
Mobilization in regards to LCNC apps and automations should include:
- User Engagement: Actively involving business users and citizen developers in the security process.
- Contextual Communication: Whether manual or automated, mobilization efforts must provide clear, actionable context.
- Threat Awareness: Offering concise explanations of potential security threats relevant to LCNC environments.
- Guided Remediation: Providing step-by-step instructions for addressing and mitigating identified security risks.
Best Practices for Integrating LCNC Security into CTEM
To successfully integrate LCNC and RPA security within CTEM, you can follow these guidelines:
- Enhance visibility: Use monitoring tools to maintain oversight of LCNC deployments.
- Prioritize high-risk assets: Focus your remediation efforts on the vulnerabilities with the highest potential business impact.
- Integrate with existing workflows: Incorporate LCNC and RPA security into CTEM remediation and incident response processes to identify vulnerabilities, automate threat detection, and continuously monitor interactions.
- Build a culture of collaboration: Promote teamwork between security, IT, and business units to strengthen oversight and maintain the security of LCNC and RPA development.
- Continuously adapt: Leverage insights from the CTEM cycle to constantly refine LCNC and RPA security processes and be able to adapt quickly as new threats arise.
A Continuous Approach to LCNC Security
As LCNC development adoption becomes more widespread across enterprises, continuous, integrated cybersecurity management becomes essential. One way organizations can stay ahead of emerging threats is by aligning LCNC and RPA security with CTEM to maintain a robust security posture. Many enterprises find this task daunting, often hesitating to look under the hood because once the issues are uncovered, they cannot be ignored. CISOs and security teams that want to adopt a proactive and comprehensive way to manage the evolving risks of LCNC applications and RPAs should integrate it with their CTEM framework.
How Nokod Can Help
Nokod Security helps businesses safeguard LCNC and RPA applications developed on platforms like Microsoft Power Platform, UiPath, and ServiceNow by continuously monitoring for potential security risks.
Nokod enables you to detect and prevent data leakage, supply chain vulnerabilities, application abuse, malicious applications, vulnerable third-party components, injection attacks, and more.
The Nokod platform facilitates proactive remediation with features such as automatic discovery and inventory of LCNC apps, policy enforcement, customizable governance rules, and automated remediation.
Nokod’s real-time visibility, reporting, and remediation tools support both security teams and citizen developers in maintaining secure, scalable LCNC application development.
Take the Next Step
- If your company wants to implement the proper oversight and processes to secure its LCNC applications, we can guide you through the first steps.
- To learn more about the Nokod Security Platform, please schedule a demo.
- To evaluate your attack surface generated by Microsoft Power Platform, don’t hesitate to use our free assessment tools.