Resources
Your friendly go-to resource for all security issues related to low-code and no-code.
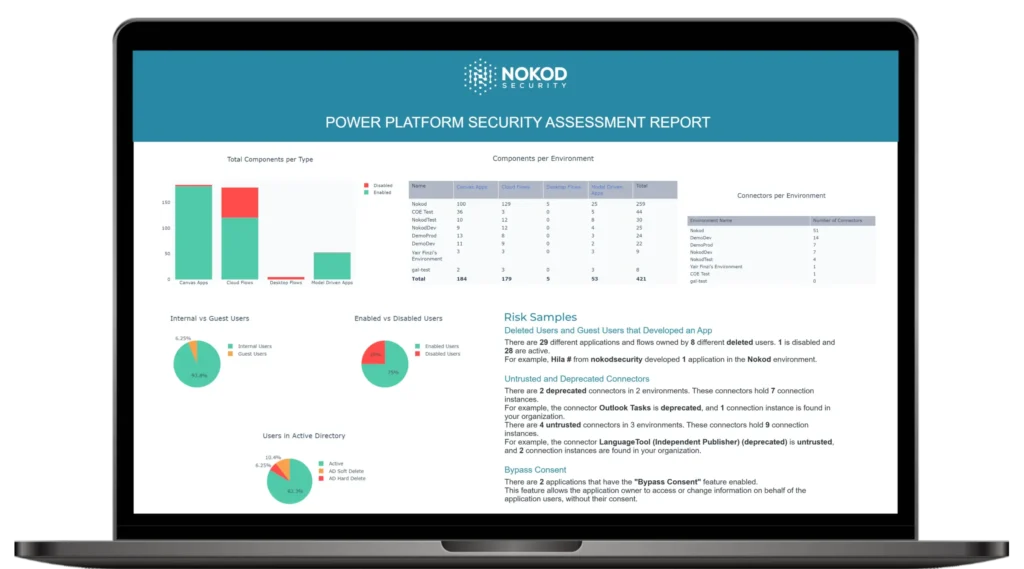
Free Power Platform Security Assessment Tools
Gain Visibility into Security Risks and Issues on Power Platform
Worried about the risks and vulnerabilities introduced by citizen development on Power Platform?
Use Nokod’s free security tools to better understand this rapidly growing attack surface and your company’s exposure.
Explore the Security Aspects of Citizen Development
The Attacker’s Path to Hacking UiPath RPAs
Leaving the attack surface created by UiPath robotic process automations unattended is more dangerous than you might think.
In this webinar, security expert Amichai Shulman demonstrates key RPA weaknesses, such as SQL injection, command injection, supply chain vulnerabilities, and container security flaws.

Power Hacking with Microsoft Power Platform
Make sure that your Power Platform low-code and no-code development doesn’t translate to low security. Watch this webinar and join security expert Amichai Shulman for a deep dive into real-world attacks, exposing dangerous misconceptions and busting the myth that Power Platform apps aren’t creating an external attack surface.

The Writing on the Wall: Security Risks in Low-Code/No-Code App Development
Webinar on demand: Watch an exploration of supply chain attacks in low-code/no-code development environments and in the marketplaces of low-code application platforms. Get practical mitigation guidelines for the attacks and mistakes detailed.
Low-Code/No-Code and RPA: Rewards and Risks
Download our practical guide to understand the fundamental characteristics and challenges, and learn how to build streamlined security into low-code/no-code applications and robotic process automations development.
Complimentary analyst report
On the Radar: Nokod offers security for low-code, no-code apps
Rik Turner, senior principal analyst at Omdia, evaluates Nokod’s platform and its coverage of vulnerabilities and risks in low-code and no-code apps.
Download our Solution Brief
Latest Articles by Nokod
June 20, 2025 – No-code platforms make building apps easy, but third-party connectors can expose you to new supply chain risks.
Amichai Shulman explains how no-code’s abstraction layer hides data flow and control, complicating security.
February 10, 2025 – No-code is booming, but is the SDLC ready? Yair Finizi’s article
discusses securing the Software Development Lifecycle for no-code apps and gives tips on how to build security into your no-code SDLC.
December 13, 2024 – In this article, Amichai Shulman exposes OData injection that poses a serious, often underestimated risk in low-code/no-code (LCNC) ecosystems, especially within the Microsoft Power Platform. This attack technique can potentially compromise sensitive corporate information by exploiting vulnerabilities that security professionals frequently overlook.
December 10, 2024 – In this article on Helpnet Security, Amichai Shulman discusses how low-code/no-code (LCNC) platforms enable application development by citizen developers and often generate “shadow engineering” projects that evade security oversight. While LCNC solutions like Power BI reports and automated workflows foster agility and innovation, they also introduce significant risks, including data leakage.
November 17, 2024 – In this article on CIO Influence, Amichai Shulman discusses how business applications and RPAs developed by citizen and automation developers are increasingly creating an external attack surface.
October 17, 2024 – In this article on Forbes, Yair Finzi discusses how the integration of GenAI and low-code/no-code development platforms is transforming organizations’ approaches to secure application development.
September 03, 2024 – Continuous threat exposure management (CTEM) – a concept introduced by Gartner – monitors cybersecurity threats continuously rather than intermittently. A prime candidate for inclusion under the CTEM umbrella is software created in low-code/ no-code (LCNC) and robotic process automation (RPA) environments.
August 7, 2024 – In his article “4 Common LCNC Security Vulnerabilities and How To Mitigate Them” on ITPro Today, Amichai Shulman illustrates the impact of low-code/no-code (LCNC) platforms, robotic process automation (RPA), and citizen development on the enterprise attack surface.
While accelerating innovation, low-code/no-code platforms introduce significant security risks, such as client-side data access issues, injection attacks, unintended public exposure, and data leakage.
June 28, 2024 – Nokod’s CTO, Amichai Shulman highlights the top security risks associated with RPA (Robotic Process Automation) and shares best practices for mitigating those risks in his latest article on SC Media.
This is a must-read if you use and need to secure automations created on platforms like UiPath, MS Power Automate, Automation Anywhere, Pega, or others.
June 26, 2024 – Yair Finzi, CEO of Nokod Security, shares his security perspective on citizen development and the use of low-code no-code development platforms.
It is striking – and worrying – how the current AppSec stack and practices fail to monitor and secure the apps and automations created by citizen developers. Yair discusses some of the root causes in his article.
June 24, 2024 – In this Forbes article, Yair Finzi, CEO of Nokod, discusses the risks of supply chain attacks in low-code/no-code development platforms (LCAP). Virtually all platforms include a marketplace for third-party components used in apps and automation created by citizen developers. Simple mistakes can lead to vulnerabilities and risks.
June 17, 2024 By Amichai Shulman, CTO at Nokod.
Like a bad movie that seems to go on forever, SQL injection (SQLi) attacks have lingered since the late 1990s. Unfortunately, a new wave of SQLi attacks is emerging—and it’s taking a different trajectory than in the past.
June 6, 2024- In the rush to digital transformation, many organizations are unaware they are exposed to security risks associated with citizen developer applications.
The Latest from our Blog

When Automation Becomes an Attack Surface: The Security Risks of UiPath
Nokod Security analyzed real-world RPA environments and found that organizations using UiPath unknowingly introduce critical security vulnerabilities which turn automations into a direct attack surface, allowing attackers to exfiltrate credentials and manipulate sensitive systems like ERPs and CRMs worldwide.
In Plain Sight: How Microsoft Power BI Reports Expose Sensitive Data on the Web
The Nokod Research Team discovered a data leakage vulnerability in the Microsoft Power BI service which potentially affects tens of thousands of organizations and which allows anonymous viewers on the Internet to access sensitive data, including employee and business data, PHI, and PII.
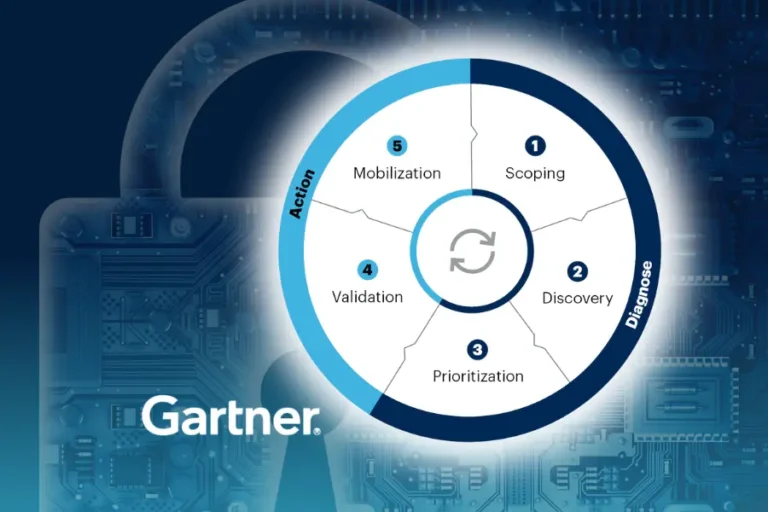
Bridging the Gap: Integrating LCNC Apps into the CTEM Framework
The rapid adoption of low-code/no-code (LCNC) development and robotic process automation (RPA) presents unique cybersecurity challenges. Incorporating LCNC and RPA into the Continuous Threat Exposure Management framework can help mitigate associated risks effectively.
Recent Press Releases

Nokod Security Mentioned in 2025 Gartner® Research on Citizen Application Development Platforms
Nokod is mentioned by Gartner as a security-specific provider that can help organizations minimize threat exposure, protect sensitive data and comply with regulatory standards.

Nokod Security mentioned in the 2025 Gartner® Research on Governing Low-Code/No-Code Applications
Nokod is mentioned as an example of a Third-Party Application Health Inventory Page in the 2025 Gartner report “How to Support and Govern Low-Code Applications for Citizen Development.”

Nokod Security Profiled in Omdia On the Radar Report for Innovation in Low-Code/No-Code Application Security
Nokod is recognized by global analyst firm Omdia for empowering enterprise security teams and citizen developers to address vulnerabilities and risks in LCNC application development.
Ready to Take the Next Step? Get a Demo.
Experience the new way to effectively secure your low-code/no-code apps. Contact us to schedule a demo with one of our product experts.
We are eager to learn about your requirements and show you how Nokod Security can benefit you, your team, and your organization.
Discover all your organization’s low-code/no-code applications and automations.
Place them under your policies to reveal governance and compliance issues.
Empower citizen developers and security teams to deal with threats right away.



