CVE-2023-36019 Affecting Microsoft Power Platform Connector
With security teams already at Christmas parties, Microsoft dropped its final security update for 2023. The December 2023 Patch Tuesday addressed a total of 36 security vulnerabilities. Of the three classified with critical severity in Microsoft advisories, CVE-2023-36019 – affecting Microsoft Power Platform Connector – caught Nokod Security’s attention. The vulnerability CVE-2023-36019 has a CVSS score of 9.6, indicating a high severity and impact level.
What do I need to do? Nokod Security customers are taking the fast lane to remediation.
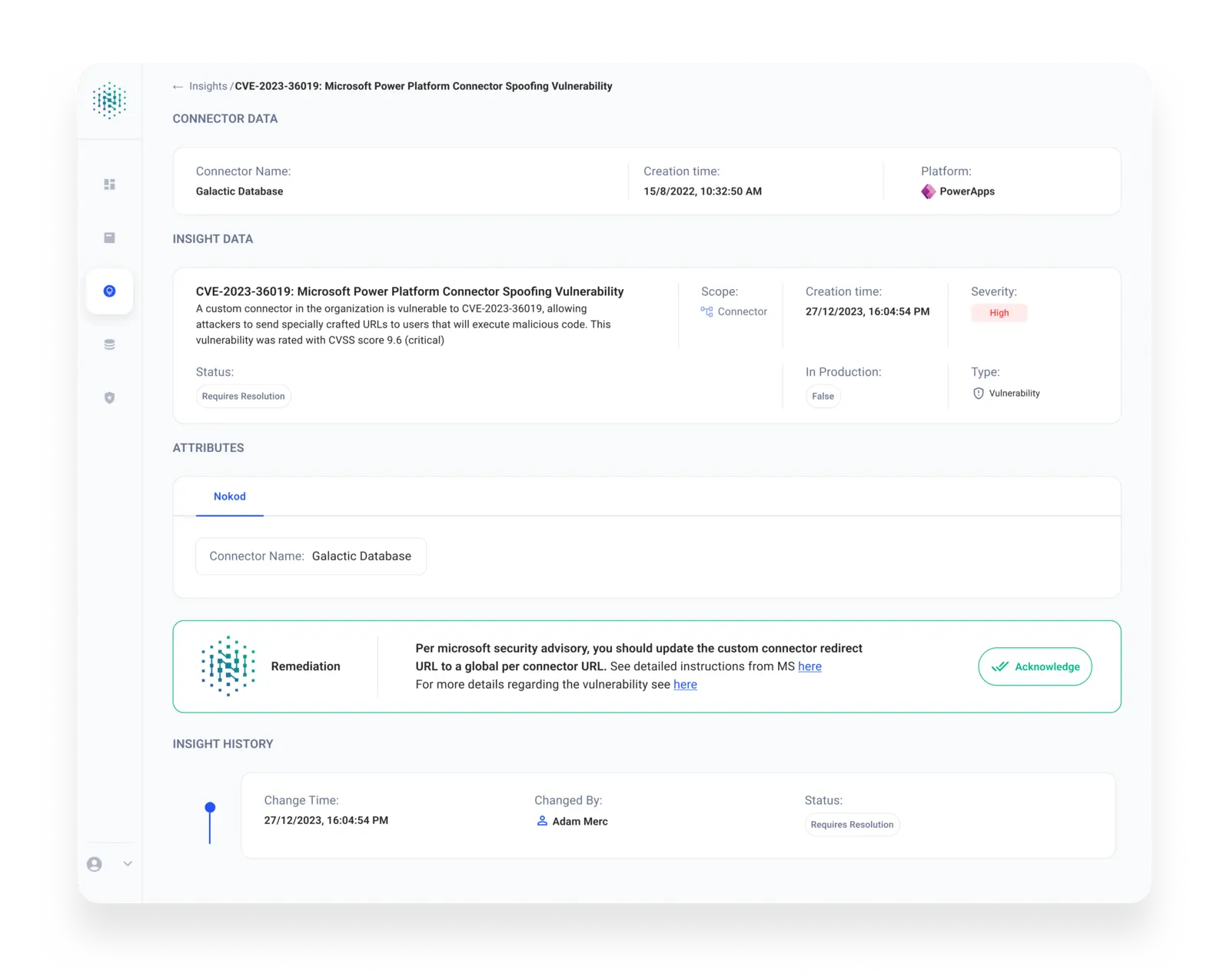
To mitigate this vulnerability, Microsoft has applied a security update that requires newly created custom connectors using OAuth 2.0 to have a per-connector redirect URI. However, all existing OAuth 2.0 custom connectors must be updated manually to use a per-connector redirect URI before February 17th, 2024. Hence, security teams need to map all vulnerable custom connectors and attend to them ASAP.
If you are a Nokod Security customer, sit back and relax – our solution lets you know through a new type of Insight which connectors need your attention.
If you are not a Nokod Security customer, look through the list of custom connectors for those who use OAuth 2.0 authentication and are configured with Global Redirect URI.
Or, contact us at [email protected], and we will help you.
CVE-2023-36019 in Detail
CVE-2023-36019 is a spoofing vulnerability that affects the Microsoft Power Platform Connector, a component that allows users to create custom connectors for various services and applications. A custom connector is a wrapper around an API enabling the underlying service to talk to Microsoft Power Platform. Custom connectors can be used to extend the functionality of low-code/no-code (LCNC) applications, such as PowerApps and Logic Apps, by enabling them to access data and actions from external sources.
An attacker can exploit this vulnerability by crafting a malicious link, file, or application that appears to be a legitimate connector and tricking the victim into interacting with it. This could result in the attacker gaining access to the victim’s data, credentials, or system resources. While the vulnerability is in the web server, malicious scripts execute in the victim’s browser on his/her local machine.
To mitigate this vulnerability, Microsoft has applied a security update that requires newly created custom connectors that use OAuth 2.0 to authenticate to have a per-connector redirect URI. Existing OAuth 2.0 connectors must be updated to use a per-connector redirect URI before February 17th, 2024. For more information, see Security Update Guide – Microsoft Security Response Center.
Takeaways
This vulnerability highlights the importance of securing low-code/no-code applications and their components, such as custom connectors and third-party components.
Low-code/no-code apps are designed to enable users with little or no coding experience to create and deploy applications quickly and easily. However, this also means that users may not be aware of the potential security risks.
While it is important to follow the security guidance and recommendations provided by Microsoft and other LCAP vendors, including applying the latest patches and updates as soon as possible – it is not enough.
It is evident from this recent incident that security teams need help in identifying vulnerable components and remediating them. Moreover, most of the security issues stem from application and flow logic and therefore do not fall under the responsibility of the LCAP vendor. It is clearly time for enterprises who (rightfully) chose the path of no-code/low-code development to deploy a dedicated security solution for LCNC AppSec.
Amichai Shulman


